Routing is a fundamental aspect of networking that determines how data packets travel from their source to their destination across interconnected networks. It involves the use of hardware and software to direct internet traffic in the most efficient and secure way possible. In this guide I will explore the intricacies of routing, including its principles, types, protocols, and the critical role it plays in the global internet.
What is Routing?
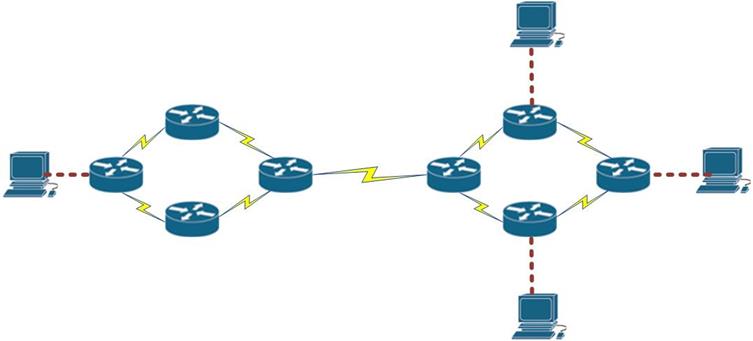
Routing is the process by which data packets are forwarded from one network to another until they reach their final destination. The devices responsible for this process are called routers. These devices use headers and forwarding tables to determine the best path for forwarding the packets.
Key Principles of Routing
- Path Determination: Routers use routing algorithms to calculate the best path for sending data across a network. The decision is based on factors such as the number of hops, network traffic, link costs, and policy rules.
- Routing Tables: Each router maintains a table called a routing table, which contains the routes to various network destinations. The routing table includes information about the topology of the network immediately around it.
- Dynamic Learning: Routers learn about the network dynamically by using routing protocols to communicate changes in real-time. This adaptability helps maintain optimal routes even as the network changes.
Types of Routing
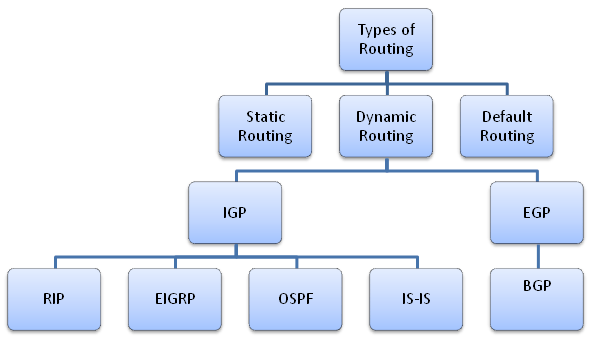
- Static Routing:
- Definition: Static routing involves manually setting the routes in the routing table through configuration files.
- Advantages: Provides an element of predictability and security, useful in small networks where network traffic and topologies are not expected to change frequently.
- Disadvantages: It is not scalable for larger networks with frequently changing network layouts.
- Dynamic Routing:
- Definition: Dynamic routing uses protocols that allow routers to communicate among themselves to update and maintain routing tables automatically.
- Advantages: More scalable and fault-tolerant, automatically adapting to network changes.
- Disadvantages: More complex to configure and can consume more network resources.
Routing Protocols
Routing protocols are vital components of network architecture, enabling data packets to be routed between nodes efficiently. These protocols are categorized into Interior Gateway Protocols (IGP) and Exterior Gateway Protocols (EGP), each serving different purposes within global and local contexts. This detailed exploration will focus on the intricacies of these protocols, especially on Border Gateway Protocol (BGP), which is pivotal in the functioning of the internet.
Interior Gateway Protocols (IGP)
IGPs are used within a single autonomous system. They are designed to be fast and efficient in routing within a controlled domain. Here’s a closer look at the commonly used IGPs:
- Routing Information Protocol (RIP):
- Operation: RIP is one of the oldest routing protocols and operates using a distance-vector routing algorithm. It utilizes hop count as its primary metric to determine the best route to a network; the maximum allowed hops in a path can be 15, beyond which the network is considered unreachable.
- Characteristics and Usage: RIP is simple to configure and works well in small, homogenous environments. It is less suitable for larger networks due to its slow convergence and limited scalability.
- Open Shortest Path First (OSPF):
- Operation: OSPF is a more sophisticated protocol using a link-state routing algorithm. It creates a topology map of the network, which it updates by broadcasting the state of its own links to all other OSPF routers within the same hierarchical area.
- Characteristics and Usage: OSPF offers faster convergence times than RIP and supports more complex network structures with its ability to segment the network into different areas, reducing routing overhead. It is highly scalable, which makes it suitable for large enterprise networks.
- Enhanced Interior Gateway Routing Protocol (EIGRP):
- Operation: Developed by Cisco, EIGRP is an advanced distance-vector routing protocol that incorporates features of both distance-vector and link-state protocols. It uses algorithms to decide the best path and supports load balancing at unequal costs.
- Characteristics and Usage: EIGRP is known for its quick convergence times, efficiency, and less overhead. It’s proprietary to Cisco but can be used in a mixed-router environment with some configuration adjustments.
Exterior Gateway Protocol (EGP)
- Border Gateway Protocol (BGP):
- Operation: BGP is the protocol backbone of the internet, classified as a path-vector protocol. BGP is used for routing between autonomous systems (ASes), which are large networks or groups of networks managed by a single organization. BGP routers use TCP connections to exchange routing information, primarily focusing on the path the data takes to reach the destination.
- Characteristics and Usage: BGP’s strength lies in its ability to handle thousands of routes and its robustness, offering stability to the internet’s routing system. It uses an extensive set of attributes that influence the path-selection process.
Deep Dive into BGP
BGP is critical for maintaining the structure of the internet. Here’s how it manages such a crucial role:
- Path Vector Mechanism: BGP uses the path vector mechanism where the best path is selected based on a sequence of autonomous systems that data must pass through. This mechanism helps in avoiding routing loops and in selecting efficient, reliable paths.
- Route Advertisement: BGP routers do not broadcast their entire routing table (which would be massive) but instead send updates only when routing changes occur.
- Attributes and Path Selection: BGP attributes like AS-Path, Next-hop, Local Preference, and MED play a significant role in path selection. The decision process evaluates these attributes to choose the most desirable path.
- Policies and Scalability: BGP’s ability to implement routing policies at an administrative level is one of its most powerful features. Policies can dictate how routers handle incoming and outgoing routes based on various attributes, allowing for a very granular control over traffic flow.
- Security and Stability: Despite its critical role, BGP faces security challenges, notably its vulnerability to hijacking and route leakage. Efforts such as implementing Route Origin Authorizations (ROA) using Resource Public Key Infrastructure (RPKI) are underway to enhance BGP security.
How Routing Works: A Closer Look
To better understand how routing works, let’s consider a practical scenario:
- Scenario: A user in New York is sending an email to a friend in London. The data packet created from this email needs to navigate through multiple networks to reach its destination.
- Process:
- The email data is converted into data packets.
- Each packet contains source and destination IP addresses.
- Routers along the path read the packet’s destination address and consult their routing tables to decide where to forward the packet next.
- Depending on the network conditions, protocols, and configurations, each router along the path makes an independent routing decision, which determines the packet’s next hop.
- The packets may take different paths to the destination and are reassembled into the original email once they arrive at the destination.
Challenges in Routing
- Scalability: As the number of network endpoints increases, maintaining efficient and correct routing tables becomes more complex.
- Security: Routing protocols can be vulnerable to various attacks, such as routing table poisoning and rerouting traffic to malicious sites.
- Performance: The choice of routing protocol and path determination strategy can significantly impact network latency and throughput.
Conclusion
Routing is a vital component of the network infrastructure that ensures data is efficiently transmitted across different network segments. Understanding the different types of routing and routing protocols helps network engineers design and maintain networks that meet the specific needs of organizations. As networks continue to grow in size and complexity, effective routing strategies will remain crucial in managing the flow of data across network borders, ensuring connectivity and performance are maintained at optimal levels.